
eLearning Project Showcase:
Hills Construction Company -
Delivering Effective Training Solutions
Hills Construction Company -
Delivering Effective Training Solutions
Description
This is a scenario-based eLearning project designed and developed to help employees improve their cyber security awareness and response skills. Throughout the course, learners engage in a series of realistic, low-risk scenarios, ultimately learning which actions help prevent security incidents and maintain a secure work environment.
Responsibilities: Instructional Design, Action Mapping (Needs Analysis), Storyboarding, Visual Design, Mockups, eLearning Development.
Tools Used: Articulate Storyline, Adobe XD, Adobe Illustrator, Vyond, PDF, Google Docs
KPI: Security incidents will decrease by 30% by December 1st as employees apply the learned cyber security practices.
The problem
Hills Construction Corporation, a mid-sized technology firm, has experienced a troubling increase in cyber attacks over the past three years, leading to severe financial and operational impacts. Between 2021 and 2023, the company faced 20 significant security incidents, including phishing attacks, ransomware, and data breaches, resulting in a total financial loss of $2.5 million. These incidents compromised sensitive employee and customer data, disrupted operations, and caused extended downtime. The analysis revealed that most employees lacked proper cybersecurity training, existing security protocols were outdated, and the incident response plan was inadequate
The Solution
The root causes of these security breaches were traced back to insufficient employee awareness and training, outdated security measures, and a weak incident response strategy. Phishing attacks were prevalent, particularly targeting mid-level employees, and the response to these attacks was slow, taking up to 72 hours to detect and address. Ransomware attacks further crippled the company’s operations, with an average recovery time of 14 days. Additionally, data breaches exposed confidential information, resulting in regulatory fines and further financial losses. This situation highlights the urgent need for a comprehensive information security strategy, including employee training, updated security protocols, and a robust incident response plan to safeguard the company’s assets and reputation.
As an instructional designer, I proposed a comprehensive approach to improve information security at Hills Construction Corporation. This included developing targeted learning solutions and recommending essential non-learning solutions.
Learning Solutions
Provided courses on cybersecurity basics, threat identification, and incident response.
Hosted sessions led by experts to discuss recent threats and practical defense strategies.
Simulated phishing attacks to test and improve employee awareness and responses.
Non-Learning Solutions
Implemented advanced antivirus, anti-malware, and encryption to protect sensitive data.
Hired dedicated security staff and consulted external experts for regular assessments.
Developed comprehensive policies for data handling and incident response, with clear guidelines for employees.
Created a detailed plan for detecting, reporting, and managing security incidents, with a dedicated crisis management team.
These solutions aimed to enhance Hills Construction Corporation’s information security, reduce the risk of cyber attacks, and protect the company’s digital assets effectively.
My Process
Following the ADDIE model, I refined each stage of my process until I was satisfied with the aesthetics, user experience, and educational content. Before finalizing development, my process involved constructing an action map, outlining a storyboard, crafting visual prototypes, and constructing an interactive model.
Once the client agreed to my idea for a cyber security learning solution, we needed to dig deeper into the problem. Following Cathy Moore’s approach, I used my experience in cyber security to guide the process. First, we set a clear goal for what we wanted the learning to achieve.
Then, we brainstormed the tasks and behaviors learners would need to do or avoid to meet that goal. We sorted these into main actions and smaller steps. Next, we looked at each action and figured out which ones were most important for reaching our goal.
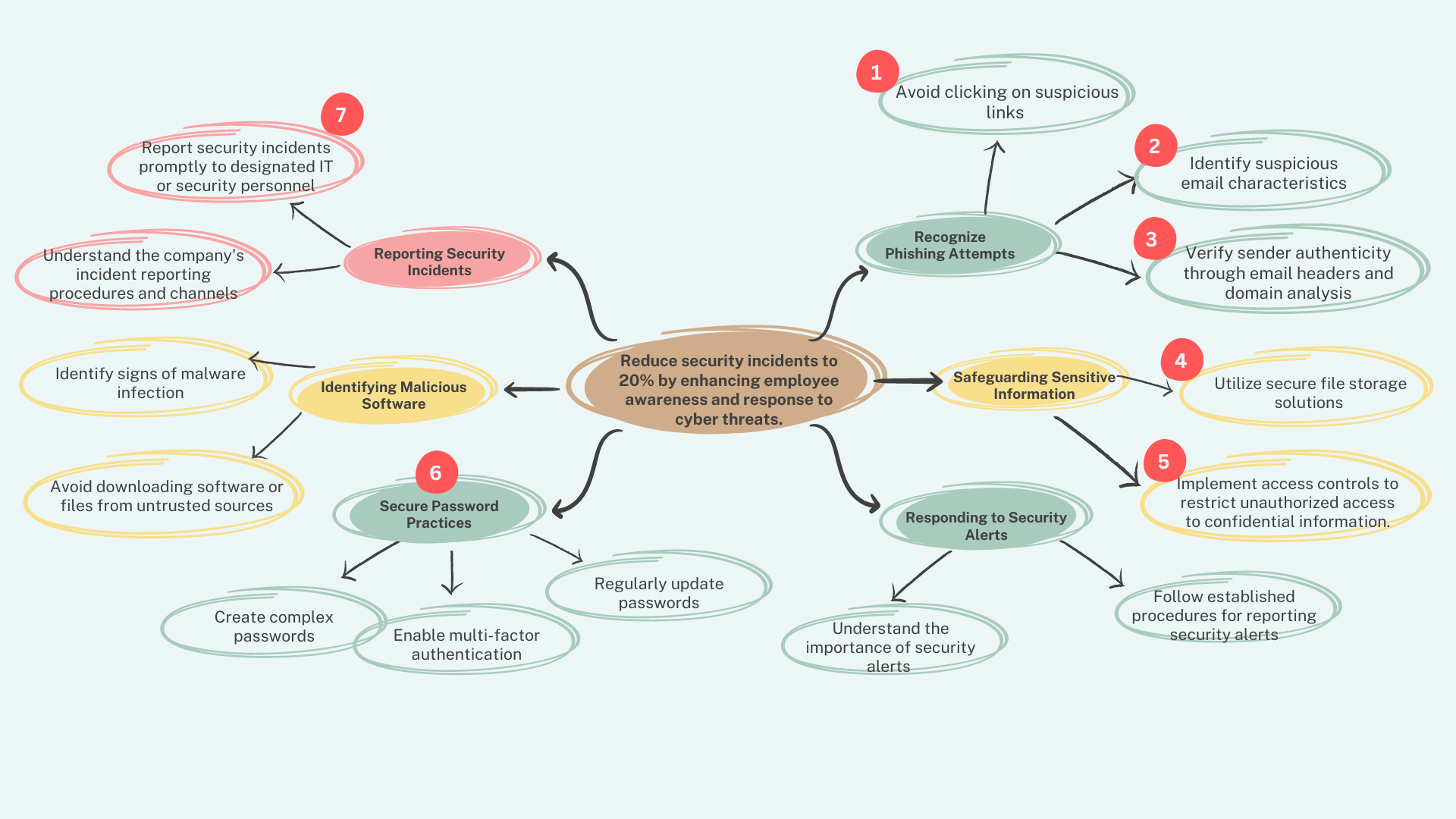
We found six key actions that became the focus of the learning content. These actions were the backbone of how we designed the learning experience. You can see them branching out from the cyber security goal in the action map below.
Action mapping is crucial because it helps me make sure the learning fits what the client wants and is useful for the learner.
Setting a clear goal helps everyone stay focused on what really matters: making sure the business succeeds. And by prioritizing actions, we make it easier for learners to remember the most important stuff they need to know.
After identifying all high-priority tasks and behaviors through action mapping, I created and refined a text-based storyboard to act as a blueprint for the final cyber security training product.
To help learners achieve the performance goal, I prioritized the main features to include in the experience. It was essential that the final product was scenario-driven and focused on the key actions identified in the action map to prevent information overload.
Another priority was to provide learners with feedback based on their choices. Using a combination of sound effects, wording, and visual design, learners would receive positive reinforcement for correct decisions. For incorrect choices, learners would see the consequences play out, learn from them, and have the chance to try again.
Once the critical assets of the course were prioritized, I had a clear path to complete the storyboard in a way that would engage learners effectively in the scenarios. I also incorporated a mentor figure to provide learners with helpful information as needed.
Working with and receiving feedback from the expert helped me develop realistic scenarios. We focused on creating a story that mirrored real-life experiences within the company. This approach helped create authentic consequences and provided a clear “why” for making correct choices.
The client reviewed and approved the text-based storyboard developed with the help of the subject matter expert.
 The storyboard was a crucial part of my design process because it allowed me to embed significant instructional practices and learning theories to create an optimal learning experience for the users.
The storyboard was a crucial part of my design process because it allowed me to embed significant instructional practices and learning theories to create an optimal learning experience for the users.Creating the visual mockups gave me a clear vision for my design, but it was the interactive prototype that truly brought the experience to life. Using Articulate Storyline 360, I developed a prototype to gather feedback on its functionality and overall development.
I included several interactive slides up to the first scenario-based question, adding triggers, animation, sound, and a success meter. Then, I shared the prototype with stakeholders and made improvements based on their feedback.
The interactive prototype showcased many features that stakeholders loved and also provided valuable feedback for enhancing the learner’s experience and allows me to improve the experience based on user testing and feedback from the client.
After ensuring my prototype looked and functioned exactly as I wanted, I created the remaining scenario-based slides. I then refined them until all animations, sounds, visuals, and triggers worked seamlessly together.

